Buzz Marketing
Buzz marketing is defined as “the promotion of a company or its products and services through initiatives conceived and designed to get the media and the public talking positively about that company, product or service”, according to Kirby and Marsden (2006, p.xviii). Buzz marketing involves word of mouth propagation of the products and services of the company through the “vibes” or the buzz created through other customers or a form of a campaign driven by customer hype, says Dye (2000). According to Carl (2006), though marketers knew the power of relationship based recommendations to be very powerful as a persuader of consumer decisions, the dimension of marketers “engineering” peer opinions in social networks is little understood. Therefore, the buzz can come from paid sources who muster up support for their opinions in their social circle or individuals who voluntarily express such opinions positive for the company and both the forms of communication can be included in buzz marketing (Carl, 2006).
The key enabler of buzz marketing is the influence the opinions of individuals have on other individuals known to them. “A third party is involved in the amplification of the initial marketing efforts of the company in his or her relational networks” (Thomas, 2004, p.64). Often, a company has loyal and disloyal customers, and the disloyal ones are more influential in spreading the buzz. The loyal customer already may have influenced his or her networks and the greatest impact for marketers lies in tapping the opinions of the disloyal customers (Carl, 2006). Therefore, the company need not rely on its own customer culture for the creation of the buzz, but can actively look for counter cultures, which can be real value additions to the campaign. This implies that not all individuals have the same level of ability to influence others. Therefore, the concern of marketers is to find the most influential set of people to create the buzz if it has to succeed in its campaign, be it its own set of customers or a group of individuals who have remained out of the influence of the marketer.
Apart from the people who spread the buzz, other factors aid in the success of the marketer. People cherish owning something that most others cannot. This must be used effectively by creating the urgency in influencing the customer decision. The endorsement of a celebrity can also trigger wide spread in buzz marketing, with the critical thing being how the celebrity is made to handle such a communication, according to Dye (2000). The author cites many examples, for instance, the books selected by Oprah Winfrey for her book club invariably become best sellers and publishers lobby to get their work featured by her.
Identifying the best sources that can start the buzz is crucial and the process of identification involves grouping customers according to their purchase behaviors (buzz marketing), understanding how each group influence the other groups, identifying the paths of influential communications through simulation and finding the strongest path and group, according to Dye (2000). The structured approach also dispels the myth that buzz cannot be planned and executed, but highly random.
One of the key approaches to creating buzz marketing strategy lies in getting the influential group of people or some individuals or an individual from the group to experience the product or the service of the company. If the company is right about the selection of the group, the buzz will be created invariably because of the Hawthorne effect; when people feel valued and feel an increase in their self-esteem in being the pioneers in using a product, goodwill is created (Kirby & Marsden, 2006). Buzz marketing can be peer-to-peer and performer-to-peer. While in the former, individuals voluntarily become brand ambassadors for the company, in the latter, the company uses carefully planned seeding into relational networks through rehearsed campaigns. Marketers can also launch covert buzz campaigns, where customers are not aware that they are being marketed to. But the downside is that when customers know that they have been part of a campaign, they may fee duped and this may lead to backlash for the company, according to Kirby and Marsden (2006).
The field of marketing has become so cluttered that customers view all marketing communications skeptically and the importance of buzz marketing comes from the fact that the concept relies on communications from non-marketing sources, which are perceived to be more trustworthy by customers, say Darke and Ritchie (2007). Therefore, when a message reaches the customer from a friend with the intent of convincing him about the superiority of a brand or a product, it is bound to be a sensitive issue in the ethical sense. While the receiver of the communication may place value on the opinion of the friend, the friend may be motivated by the financial and other benefits from the company (Petty & Andrews, 2008). Thus, buzz marketing poses a big ethical question on the marketing community – to what level can marketers legally invade the lives and relationships of individuals in a conscientious manner.
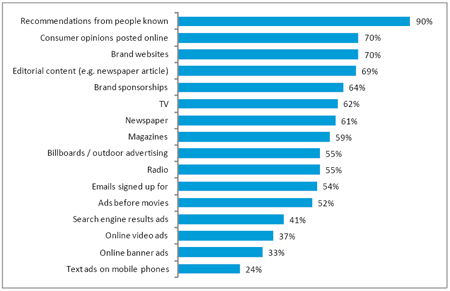
According to research, the best way to ensure that the campaign is ethical is by being completely transparent to customers and the influencers in the initial stages of the campaign and that the credibility and the trustworthiness of the influencer were not negatively affected by disclosure of the affiliation of the latter with the marketing company (Creamer, 2005; Carl, 2006). Most covert communications happen to ensure the credibility of the influencer is not affected through any disclosure of benefits or affiliation to the brand or the product of the company. Such fears seem to be unfounded, considering the impact of any adverse reactions from customer who realize that they have been marketed to at a later stage.
The role of the internet in buzz marketing is being studied by marketers and the role of internet based social networking portals needs to be understood better. Though there is much hype about the potential of the internet in buzz marketing, the reality is that face-to-face interactions carry more influence compared to an online opinion from an acquaintance or a friend (Carl, 2006). But the potential of this media is very high, as the sophistication of social networking portals is increasing and the level of interactions which are happening between individuals at a great distance to each other physically is becoming higher (Kirby & Marsden, 2006). Therefore, the role of the internet cannot be ignored as the principal tool for buzz marketing in the future.
Corporate Reputation Management
According to the resource based view of management, organizations with valuable and rare tangible and intangible assets enjoy competitive advantage in the market and can be expected to yield superior returns. When the assets are not easily imitable by competition, the advantage of the company can be sustained for superior value creation and market dominance; corporate reputation is one such intangible asset that cannot be replicated by a competitor in the short term, according to Roberts and Dowling (2002). According to Fombrun and Riel (1997), it is relatively unexplored as a concept and its importance is realized only when it is threatened.
Corporate reputation is the collective opinion of the stakeholders of an organization based on its past record, according to Nakra (2000). Reputation management is about building and maintaining the repute of an organization and generating positive feedback or word of mouth. The reputation of a company not only impacts the ability of the company to sell its products, but also in securing investments, shareholder confidence, governmental support and hiring talented employees (Nakra, 2000). Once lost, it is very difficult to regain, says Winkleman (1999). This concept comes within the function of public relations and corporate communications, which concern how the organization is viewed by its different stakeholders (Nakra, 2000). While organizations have measures and checks and balances for the other performance parameters of the organization, including effectiveness, financial performance and other tangible factors, the factor of the reputation of the organization that aids in the achievement of the overall goals of the organization are not measured and grossly ignored (Nakra, 2000). This is critical for a robust buzz marketing campaign.
Reputation management for organizations is important due to the changing dimensions of product marketing, diverse communication channels, mergers and acquisitions and high levels of global activism against corporates, say Argenti and Druckenmiller (2004). As businesses go global, they face a number of public relations issues, in having to deal with a new culture and policy environment and this necessitates a good corporate reputation for the process to be smooth (Pinkham, 1998). Customer expectations from companies have also become more stringent, with more choices available. Customers base their decisions based on the level of information available about the company and the reputation of the company before committing to a deal (Nakra, 2000).
Reputation of organization arises from the past, where the actions and performance of the organization in various aspects determine the present reputation. Stake holders consider the performance and success enjoyed by the organization, especially the financial performance as an important indicator of the goodness of the organization, according to Roberts and Dowling (2002). In fact, the correlation between the financial success of the firm and its reputation can be very high. A reputed firm will be able to charge a premium for its products and services from the market. It also has the benefits of being able to attract and retain the best talent in the industry at the lowest possible costs among its competitors. It will be able to generate more value from its supply chain and thus be able to save costs, resulting in higher margins and realizations. Similar relationships are visible in the function of buzz marketing too; reputed organizations are able to sell more with a lower effort at the best prices, due to its superior products, better sales force, better channel partners and a number of other enablers, according to Dowling (2001). These are the views of the external world of the reputed organizations or the collective perception of the market or the society on the characteristics of the firm. This means that to manage reputation, organizations have to be critical of all their interactions with the stakeholders and society, as each of these interactions, from a product launch to a simple customer query have the potential to enhance or spoil the reputation of the company.
Buzz Marketing Reputation
The reputation of the organization is deeply embedded within the experiences of the employees of the organization and manifests itself as a dimension of the working culture. When an organization is reputed and this is part of the organizational perceptions of the managers in the company, the nature of their interactions with their employees and other stakeholders will be in the manner which safeguards the reputation, say Fombrun and Riel (1997). The culture of the organization is manifested in the behaviors and attitudes of the individuals and in their interactions with each other; the organizational reputation becomes an invisible part in the culture and influences it, according to the authors. Therefore, the actions of the individuals and their perceptions within the organization, or the internal identity of the organization is manifested to the external world by means of its corporate reputation (Fombrun & Rindova, 1996). The organizational culture, therefore, plays an important role in determining the reputation of the organization to the outside world, through its policies, stand on its role in society and its responsibility to the world and how these are perceived by the stakeholders.
The reputation of an organization cannot be managed if the perception of society is not considered in the picture. Corporate social responsibility (CSR) is a philosophy advocating that organizations have a moral responsibility in helping overall social development and uplift through strategic philanthropic activities, according to Carroll (1991). The sustainability of organizations depends on the environmental, social and financial sustainability (Wempe & Kaptein, 2002). The role of philanthropy and other social benefits in the development of the reputation of an organization cannot be ignored. Organizations sometime spend more on advertising their good work than doing the good work (Alsop, 2002). This has led people to view corporate philanthropy as designed for corporate gain in some covert fashion (Porter & Kramer, 2002). This can be potentially damaging to the reputation of firms. The social responsibility when met has to be advertized at the right levels of austerity. If this is not executed properly, either the organization will be accused of doing too little or of being too brash in its claims of being a caring social entity. Therefore, the CSR activities of organizations are an effective tool for the management of corporate reputation and buzz marketing.
References
Alsop, R. (2002). Perils of corporate philanthropy. Touting good works offends the public, but reticence is misperceived as inaction. The Wall Street Journal, 16 Jan 2002, Print Edition.
Argenti, P. & Druckenmiller,B. (2004). Reputation and the corporate brand. Corporate Reputation Review, Vol.6, No.4, pp.368-374.
Carl, W. (2006). Whats all the buzz about? Everyday communication and the relational basis of word of mouth and buzz marketing practices. Management Communication Quarterly, Vol.19, No.1, pp.601-634.
Carroll A.B. (1991). The pyramid of CSR: toward the moral management of organisational stakeholders. Business Horizons, July/August(1991), pp.39-48.
Darke, P. & Ritchie, R. (2007). The defensive consumer: advertizing deception, defensive processing, and distrust. Journal of Marketing Research, Vol.44(Feb), pp.114-127.
Dowling, G.R. (2001). Creating corporate reputations using buzz marketing. Oxford: Oxford University Press.
Fombrun. C & Riel, Van C. (1997). The reputational landscape. Corporate Reputation Review, Vol.1, No.1&2, pp.5-13.
Fombrun, C.J. & Rindova, V. (1996). Who’s Tops and Who Decides? The Social Construction of Corporate Reputations’, New York University, Stern School of Business, Working Paper.
Kirby, J. & Marsden, P. (2006). Connected buzz marketing: the viral, buzz and word of mouth revolution. Oxford: Butterworth-Heinemann. ISBN: 978750666343, 075066634X.
Nakra, P. (2000). Corporate reputation management: CRM with a strategic twist? Public Relations Quarterly, Summer(2000), pp.35-42.
Petty, R. & Andrews, C. (2008). Covert buzz marketing unmasked: a legal and regulatory guide to practices that mask marketing messages. American Marketing Association, Vol.27, No.1, pp.7-18.
Porter M.E. & Kramer, R.M. (2002). The competitive advantage of corporate philanthropy. Harvard Business Review, December 2002, pp.18-27.
Pinkham, D. (1998). Corporate public affairs: running faster, jumping higher. Public Relations Quarterly, Summer(1998), pp.33-37.
Roberts, P. & Dowling, G. (2002). Corporate reputation and sustained superior financial performance. Strategic Management Journal, Vol.23(2002), pp.1077-1093.
Thomas, G.M. (2004). Building the buzz marketing in the hive mind. Journal of Consumer Behaviour, Vol.4, No.1, pp.64-72.
Winkleman, M. (1999). The fickle finger of reputation. Chief Executive, Vol. 44, No.1, pp.79-86.
Wempe, J. & Kaptein, M. (2002). The Balanced Company: a Theory of Corporate Integrity. UK: Oxford Univ. Press.





