Project Management Constraints
Efficient project management has become one of the most popular tools for both private and public organizations as project handlers have sought ways to improve their operations. Project managers seek to achieve success across all sectors when handling a project. Technological advancement, new product development and streamlining of business perspectives are examples of targets set by project managers. During the inception of a project, there is the careful planning, organizing and prioritizing available resources achieving the desired outcome or the projected results in the least. At the inception stage, a project seeks to achieve the set target within minimal time while using the least amount of resources. However, every project manager faces challenges during the implementation of a project. Such challenges arise from the presence of different constraints within project management.
Background of the study
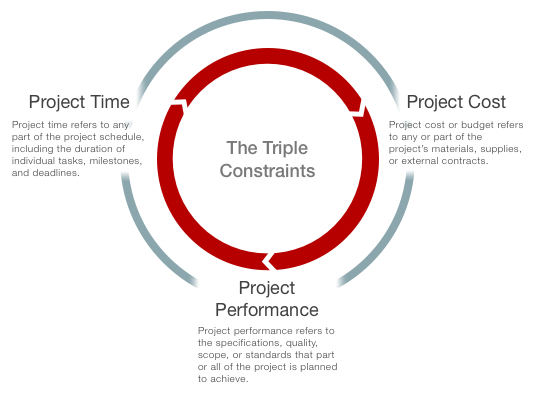
Even though a project manager prefers to achieve success all through, there are instances where resources allocated become minimal. Timeframe awarded to a project may also exceed leading to the scope of a project taking a new approach. Project constraints hinder project success hence the need to address each constraint. Despite the fact that project constraints are not consistent, schedule, resources and quality seem to be popularly present hindering success. The omnipresence of these three constraints has led to the name triple constraints, and this research study will address these constraints discussing how they affect project success (Kendrick, 2009).
Making a project successful within the triple constraint proves to be a challenge for every project manager. Regardless of whether its quality, resources or time, the three elements have the notion of working in tandem manner. Significantly, the absence or scarcity of one of these elements adversely affects the triumphant completion of projects. An efficient project manager comprehends that the main key of achieving success for a project entails the balancing of the triple constraints (Dobson, 2004).
Research methodology
The research methodology involved entails a presenting approach adopted within the study. Careful analysis of the triple constraints will be presented. The analysis will involve illustrations of various ways in which such project constraints affect the successful completion of a project. The approach taken will require meeting the expectations of the constraints of project management. The approach taken requires meeting the expectations of constraints in project management. Such entails the researcher to espouse a comprehensive research methodology enabling the understanding of project constraints adverse effects.
Approach
In order to remain consistent with this research, there is the approach of extensive methodologies adopted to assist readers in achieving the required results. There were appropriate considerations of projects that have failed or succeeded. Essential to this study, it is significant for a project manager to identify basic project management aspects in order to determine the purpose of a project. Such allows the understanding of project constraints leading to identifying ways of overcoming the constraints (Russell, 2011).
Project Constraint – Quality and Scope
Functions, features, content and data all constitute the scope of work to be done for any project. In order to achieve quality for any piece of work to be done, a project manager is required to provide a precise and specific statement identifying the desired final result of the project undertaken (Dobson, 2004). Every project should have a well-defined and articulate scope of work. However, it is essential to note that the scope of a project is dependent on the output quality. The output quality is essential since it ensures that a project scope is achievable.
Notable to this research, project scope requires effective planning, use of available resources, and proficient management techniques achieving the set target. Failure to adhere to such aspects will frequently lead to project failure. Mandatory for any project manager, changing the scope halfway through the project is suicidal, and often leads to project failure. Nonetheless, every project requires minor changes that are permissible during implementation in order to ensure success (Kendrick, 2009).
The quality of work done is dependent on a project manager’s understanding of project outcomes. Prior to proceeding on with a project, the client will usually have issued instructions on the expected outcome of an assignment. Nonetheless, several prospects of divergence will ensue regarding the necessity to stabilize around the existent resources. A competent project manager has the ability, and resources to cultivate success among projects undertaken. Organizations need to realize the significance of succeeding in projects as these increases their clientele base.
The project manager should have subdivisions that enable tasks undertaken within an organization (Goodpasture, 2004). There are assorted personnel dealing with the diversified projects. For instance, the manager is responsible for overseeing that the objective of the project is realized. The manager is also responsible for directing vast and significant decisions to avoid project failure. Executing this in a resourceful manner requires the program manager to ensure discipline and order is present among supervisors and other member staff.
Project Constraint – Time and Scheduling
Being the primary consideration, time management should be analyzed to the smallest detail. A competent project manager realizes the essentiality of analyzing the required time, and component to ensure successful completion of a project (Dobson, 2004). After careful analysis, each of the components is broken down in order to assign specified amount of time for handling a particular task. A project undertaken requires such aspects since they allow the estimation of a period with which the project can be undertaken. Apart from the estimation of the project period, resources required are identified to ensure success.
Despite the three constraints having a correlation to one another, time management within a project is seen as a diverse unit. Such view is alongside the realization that proper execution of any project within the allocated time is dependent on circumstances and efficient techniques. Project failure may occur despite the project manager having allocated a specific timeframe for each task. Failure can occur should there be exact resources to handle a project (Goodpasture, 2004). Abrupt emergencies may require the use of more resources in handling scrupulous tasks, leading to limited resources. The limitations of resources will often lead to an extended time-frame for a project risking failure (Russell, 2011).
Most project failures have resulted from undermining time allocated to different tasks. However, this often occurs when a project manager is unfamiliar with tasks undertaken. Failure of a project will frequently arise from unexpected events, risks and uncertainties. If the project manager is deemed to be inexperienced, the rise of potential risks will prolong the previously allocated time. Present in most projects undertaken, there ought to be an effective organization, proper restructuring and estimation techniques. Such will ensure that time is managed in an effective manner reducing the risk of failure for undertaken projects.
Project constraint – Cost and Resources
A competent project manager realizes that success of a project is compliant with the readiness and available resources. Even though time has been allocated to different tasks, it is also essential to allocate needed resources to complete the tasks at hand. However, providing the needed resources requires a project manager to have the capital needed to acquire the necessities. Such aspects require wholesome efforts on all levels of accountability. Ranging from casual workers, permanent employees, middle and top level managers, successful project completion requires collaborated efforts from parties involved. Realizing that resources like manpower are the most essential in achieving success, a resourceful project manager ought to ensure that the needs and requirements of labour present is met. Resources pose as the greatest risk in project failure (Wysocki, 2011). There are variables present like rate of materials, machinery and equipment, labour expenses which determine success or failure of a project.
Depending on market prices, the rate of materials seems to be at a constant change requiring the individual assigned to be per with the new prices. The new prices of different prices lead to subsequent changes in quality. There ought to be available capital to purchase high quality materials. For instance in building constructions, it is paramount to purchase quality materials, and failure to do so has a definite chance of project failure resulting from building collapse (Goodpasture, 2004). The purchase of machinery and equipment is also determined by price ranges within the market. However, in order to ensure success, there needs to be the use of high quality machinery and equipment.
Project running is comparative to embrowning a project plan comprehensive of the scrupulous objectives and missions. In addition, there ought to be a quantification of the assets required, the accounts should be indomitable within a timeline that is set. There is the existence of a variety of gear that is essential in making projects undertaken to be successful. The responsibilities of the manger should be as minimal as possible to avoid exhaustion from too much pressure to perform. Essential to this study, it is essential to identify different project phases and measure the success. However, the project manager should ensure that the manpower available is well taken care of since they are the success of any organization.
Conclusion
The prioritization of the constraints within a project is the foremost task needed to be undertaken by a project manager. In addition to the development of strategies in the management of multiple constraints, it is also instrumental that a project manager effectively maintains communication with the client. This ensures that they are both on the same page and that the client’s expectations are being met. Additionally, any competent project manager must ensure that they have a thorough knowledge of project management skills. This greatly assists them in being able to effectively and efficiently cater for any unforeseen project constraints. The act of balancing a project’s responsibilities is facilitated by the project manager’s ability to chart, analyze and implement it. This is because the project manager is aware of and has experience with a project’s concurrent risks.
References
Dobson, M, S. (2004). The Triple Constraints in Project Management. Arizona: Management Concepts.
Goodpasture, J, C. (2004). Quantitative methods in project management. Arizona: J. Ross Publishing.
Heldman, K. (2011). PMP Project Management Professional Exam Study Guide. USA: John Wiley & Sons
Kendrick, T. (2009). Identifying and Managing Project Risk: Essential Tools for Failure-Proofing Your Project. Phoenix: AMACOM Div American Mgmt Assn.
Russell, D. (2011). Succeeding in the Project Management Jungle: How to Manage the People Side of Projects. Phoenix: AMACOM Div American Mgmt Assn.
Wysocki, R, K. (2011). Effective Project Management: Traditional, Agile, Extreme. New York: John Wiley & Sons.